We design custom 404 pages for your site so that you can make the best out of an unfortunate situation when your clients get lost. 404 pages done well can be entertaining as well as help your clients back to your site through some actions that benefit you both.
Why do they happen?
404 errors can occur on websites from time to time when a client is able to communicate with a server but the server can’t find the page requested. This could be due to the page having been removed (or moved and the URL was not changed). Or it could be because there is a typo in the address bar.
Whatever the case, it’s a good idea to anticipate the error with a strategy to help keep your brand in good stead and your client not only helped but entertained, even leaving them in good humor where possible.
What does a custom 404 page look like?
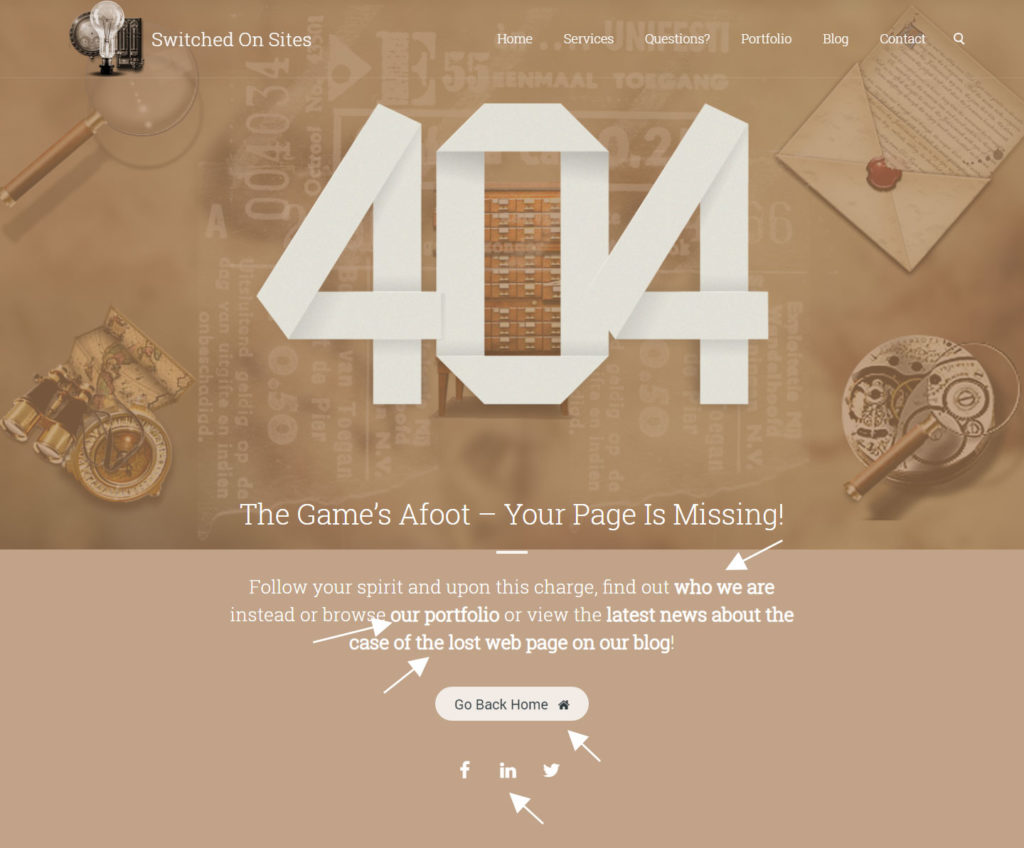
Below is our own 404 page as an example. Note that there are no less than 5 alternatives to allow your client to get back to doing something on your site. They can go to your about page, browse your portfolio, go to your blog, go back to your home page or check your social media out. They can even complain on your contact page and let you know what page they were trying to get to.
Give us a call (317.747.0622) or contact SOS if you want to add a custom 404 to your site so that you don’t lose important clients. Custom 404 pages start at $100. Don’t wait and don’t lose potential clients. SOS – Help for your website when you call.
 Switched On Sites
Switched On Sites 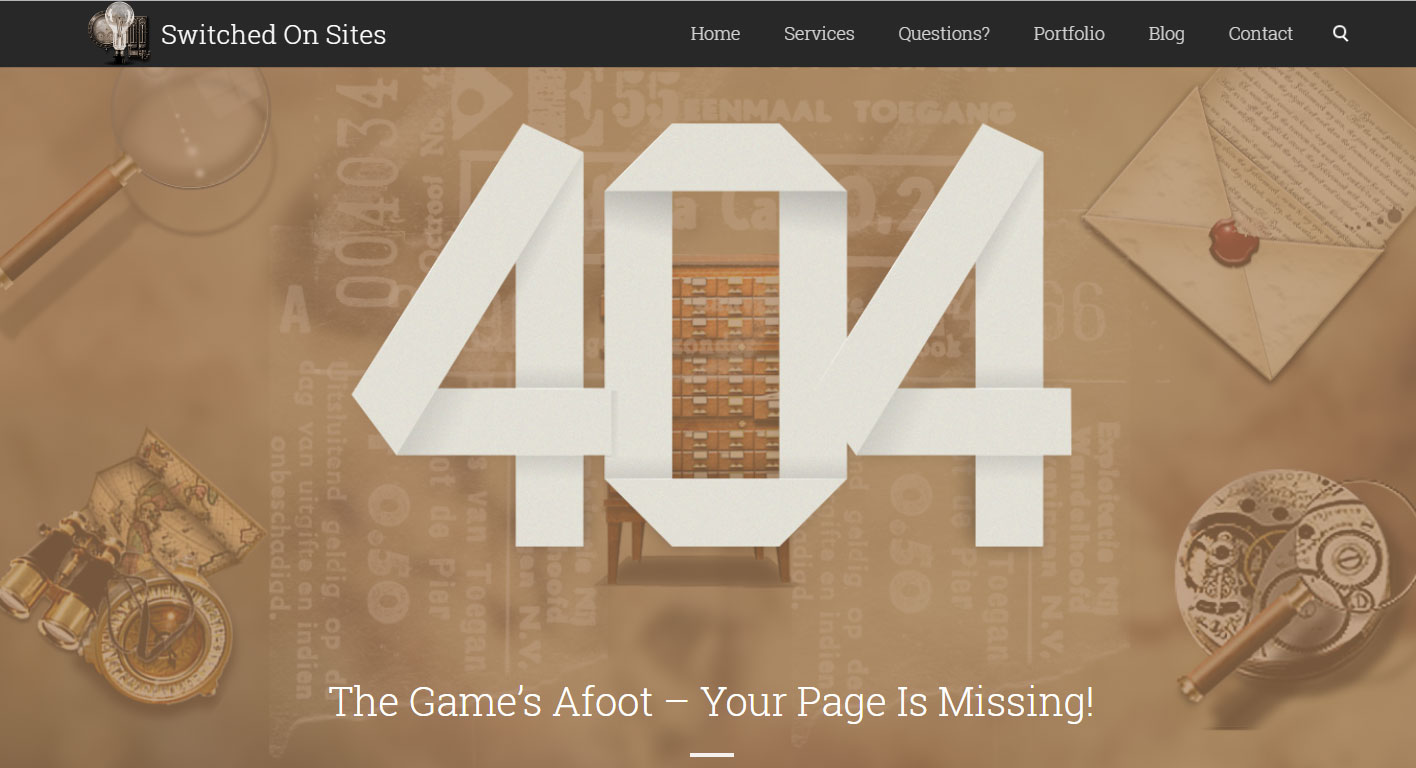








 Strange “likes” and Posts Showing Up On Your Account? You May Have Malware
Strange “likes” and Posts Showing Up On Your Account? You May Have Malware
 You didn’t just use “iloveyou” or “monkey” for your password, did you?
You didn’t just use “iloveyou” or “monkey” for your password, did you?

 Cryptoware Through Malicious Ads
Cryptoware Through Malicious Ads Are 301 Redirects Helping Your SEO?
Are 301 Redirects Helping Your SEO?
